Iran seems to have shelved its plans to carry out another large-scale direct military attack on Israel. At least for now. The scope of Israel’s previous military response, the ceasefire in Lebanon, and Trump’s looming inauguration all make this a bad time for Iran to play the naked aggressor.
But the ayatollahs are still desperate to save face with some kind of substantial strike against the “Zionist regime.”
See related: ‘We are totally outgunned,’ Iranian soldier inadvertently admits to Israeli media
In recent months, the Israel Security Agency (Shin Bet) has exposed at least 200 phishing attempts by Iranian operations with the suspected intent of facilitating assassinations.
The phishing campaign targeted a wide spectrum of Israeli figures, including high-ranking security officials, political leaders, academics, media professionals, journalists, and others.
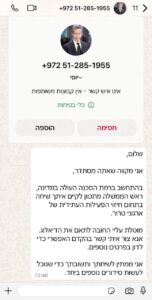
Example of a phishing attempt received by an Israeli official, informing him or her that the Prime Minister wished to consult with them.
The goal of the Iranian campaign was to gain access to the digital media (email, computers, smartphones) of Israeli individuals they aimed to target, in order to extract personal information such as home addresses, personal connections, and places they frequent regularly. This information was intended to be used by Iranian operatives to carry out attacks against individuals in Israel, using Israeli cells recruited domestically. It should be noted that in recent months, the Shin Bet and the Israel Police thwarted nine attempts by Israelis recruited by Iran to carry out missions within Israel.
As part of the Shin Bet’s operations, approximately 200 different cyberattacks on the devices and computers of Israeli individuals were identified. Iranian operatives typically approached their targets through platforms like WhatsApp, Telegram, or email, crafting personalized cover stories tailored to the target’s area of interest, so the approach would not seem suspicious.
The method: The Iranian operatives’ aim was to convince the target to download an application that would install malicious tools on their computer or smartphone, or to redirect them to a fake website mimicking a legitimate service, where they would be prompted to enter login credentials for their personal or organizational email accounts. Once the target completed one of these actions and provided their email and password, the attacker would “steal” the credentials and gain access to the target’s email or computer.
After identifying the campaign and conducting a prolonged investigation to understand its scope and locate affected citizens, the Shin Bet initiated a broad operation to notify the relevant individuals, instructing them on preventive measures, personal security, and how to enhance their digital security settings.
A Shin Bet official described this as an additional significant component in Iran’s ongoing campaign against Israel, aimed at facilitating assassination attempts. The official urged the public to remain vigilant, as such cyberattacks can often be prevented through awareness, caution, suspicion, and proper online behavior.